New Android Malware Uses Motion Sensor Data to Avoid Detection by William Chalk
Despite Google’s recent efforts to bolster and tighten the curation of its Play Store apps, shady software has once again managed to bypass anti-malware protections in order to infect unsuspecting Android users.
According to a report by Trend Micro, this new strain of malware is using an innovative new trick to avoid detection. By monitoring the motion-sensor input of an infected device, the malware stays inactive and effectively hides itself from monitors until it detects movement from its target.
The thinking behind this strategy is that sensors in real end-user devices will record motion as people use them. By contrast, methods used by analysts – and possibly Google employees screening apps submitted to the Play Store – are less likely to use sensors.
In the curation and testing process, researchers typically use emulators to detect any malicious software embedded in an application. These sandboxed emulators aren’t coded to simulate motion by default.
The authors of this new strain have taken full advantage of this loophole, creating code that stays dormant if both the device and user are still. Once traditional testing has been evaded and the apps are downloaded onto devices with a motion sensor input, it reactivates.
As soon as it detects motion sensor data, the app runs the malicious code and tries to trick unwitting victims into downloading and installing the payload with a fake system update fronted as a “stable version of Android”.Based on code similarity and a shared command and control server that’s known to have targeted Android in recent years, the Trend Micro research team have linked this payload with the Anubis banking Trojan, which can steal sensitive information from users.
Anubis uses a built-in keylogger to steal users’ vulnerable account credentials. It can also obtain this information by taking screenshots of the infected device’s activity.
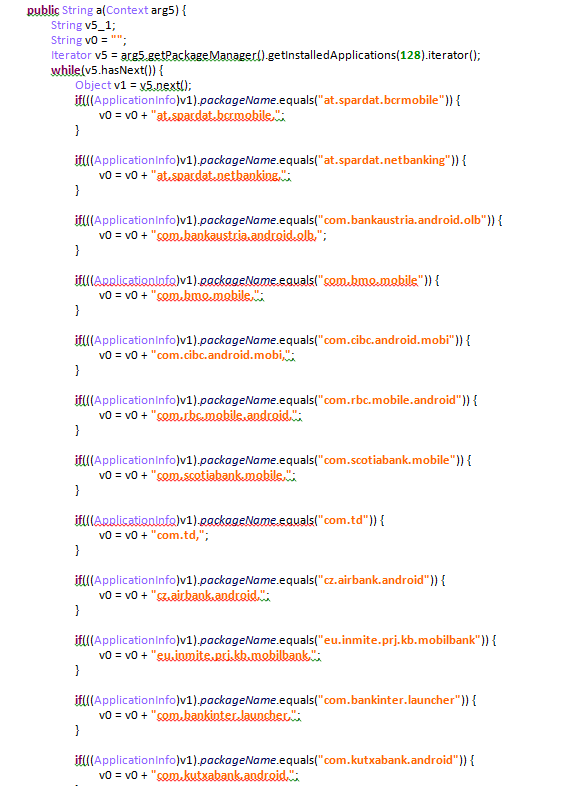
Trend Micro’s data shows that the latest version of this software has been distributed to 93 different countries and targets the users of 377 different financial apps. The report provides the following screenshot showing just some of the financial apps Anubis targets:
If Anubis successfully runs, attackers gain access to contact lists as well as location data. They can also record audio, send SMS messages, make calls, and alter external storage. Anubis can use these permissions to send spam messages and calls or even function as ransomware.
The apps in question, which feigned legitimacy by posting a large number of fake five-star reviews, masqueraded as a currency exchange app called Currency Converter and a battery saver app called BatterySaverMobi. Both the apps have since been removed from the Google Play Store.
Motion detection wasn’t the only clever feature of these malicious apps. In one example, once Anubis had been installed through the fake system update, the dropper used requests and responses over legitimate services like Twitter and Telegram to locate the required command and control (C&C) server.
App developers hid the malicious server by encoding it in the web page requests of these services, requesting Telegram and Twitter only after the running device is fully trusted.Once registered with the C&C server, it checks for commands with an HTTP POST request. If the server responds to the app with an APK command and attaches the download URL, then the payload will be dropped in the background.
At approximately 5,000 total downloads at the time of removal, the apps were identified before further damages could be wreaked. That being said, this latest breach demonstrates the evolution of malicious app codes and calls into question the trust we place in Google’s curation of its store. As malicious software improves, so must our ability to identify and apprehend illegitimate applications.
Although it is an inevitable concern, the most effective way of protecting against this kind of malware is vigilance when downloading any application – even from legitimate sources like the Google Play Store. More importantly, end-users must be discriminatory in which apps they give administrative rights to, as it is a powerful permission that can lead to full control of your device.
Clearly, the quality of malicious Android applications is improving. That being said, the functional benefit of both of these now-removed apps was minimal. Generally speaking, it’s wise to stick to a small number of applications from well-recognized developers.
William Chalk is a cybersecurity researcher at Top10VPN.
The post New Android Malware Uses Motion Sensor Data to Avoid Detection by William Chalk appeared first on Hakin9 - IT Security Magazine.
from Hakin9 – IT Security Magazine https://ift.tt/2IrDFuL

Comments
Post a Comment